-
Automated CSV Log Processing
Continuously scans one or more configured "incoming" folders for new CSV files. Parses and sanitizes
CSV rows, validates column headers, and supports multiple log categories (antivirus, firewall,
etc.).
Dynamically creates database tables based on CSV filenames and supports flexible header mapping.
-
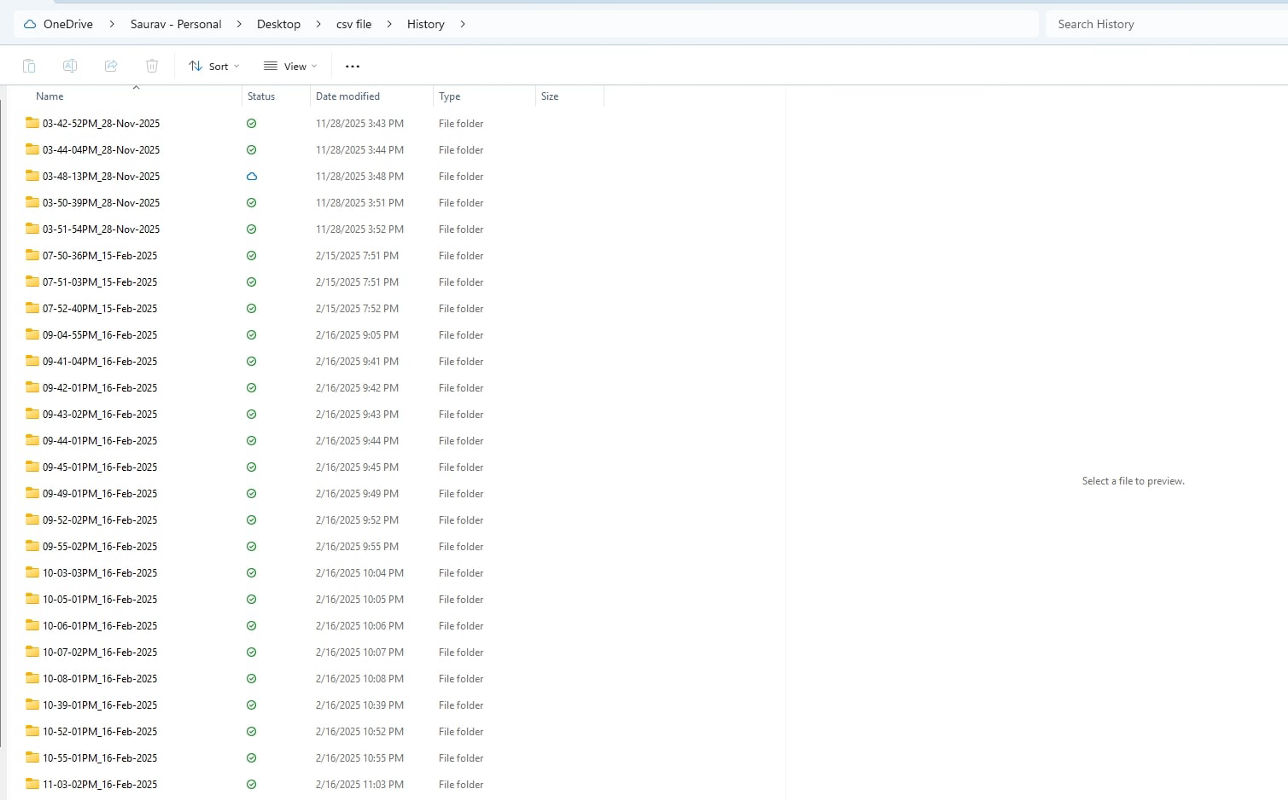
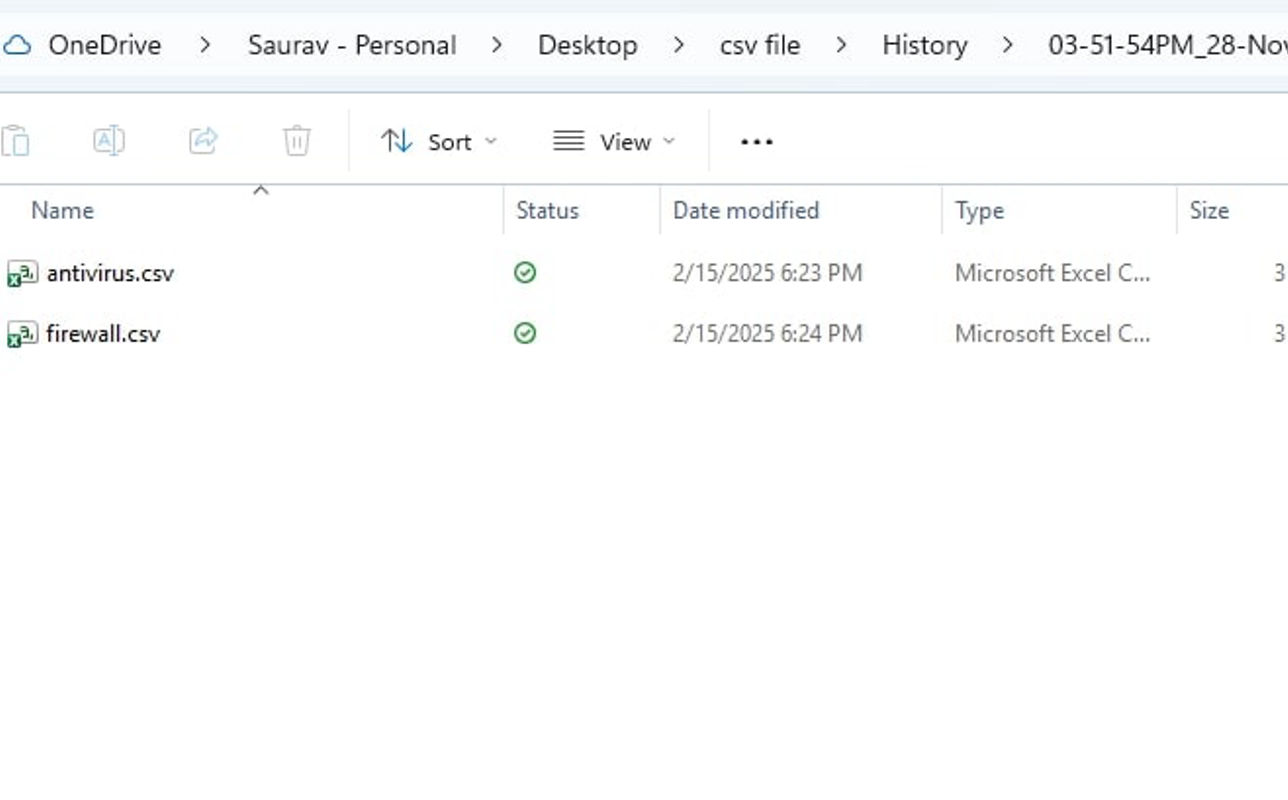
Historical File Archiving (History Folder)
After successful insertion into the database, each processed CSV file is moved to a
/history directory.
/logs
/incoming
/history
/2025-01-01_10-30-45
antivirus_20250101.csv
/2025-01-01_12-15-00
firewall_20250101.csv
Preserves originals for audits and investigations, prevents duplicates, and ensures full
traceability.
-
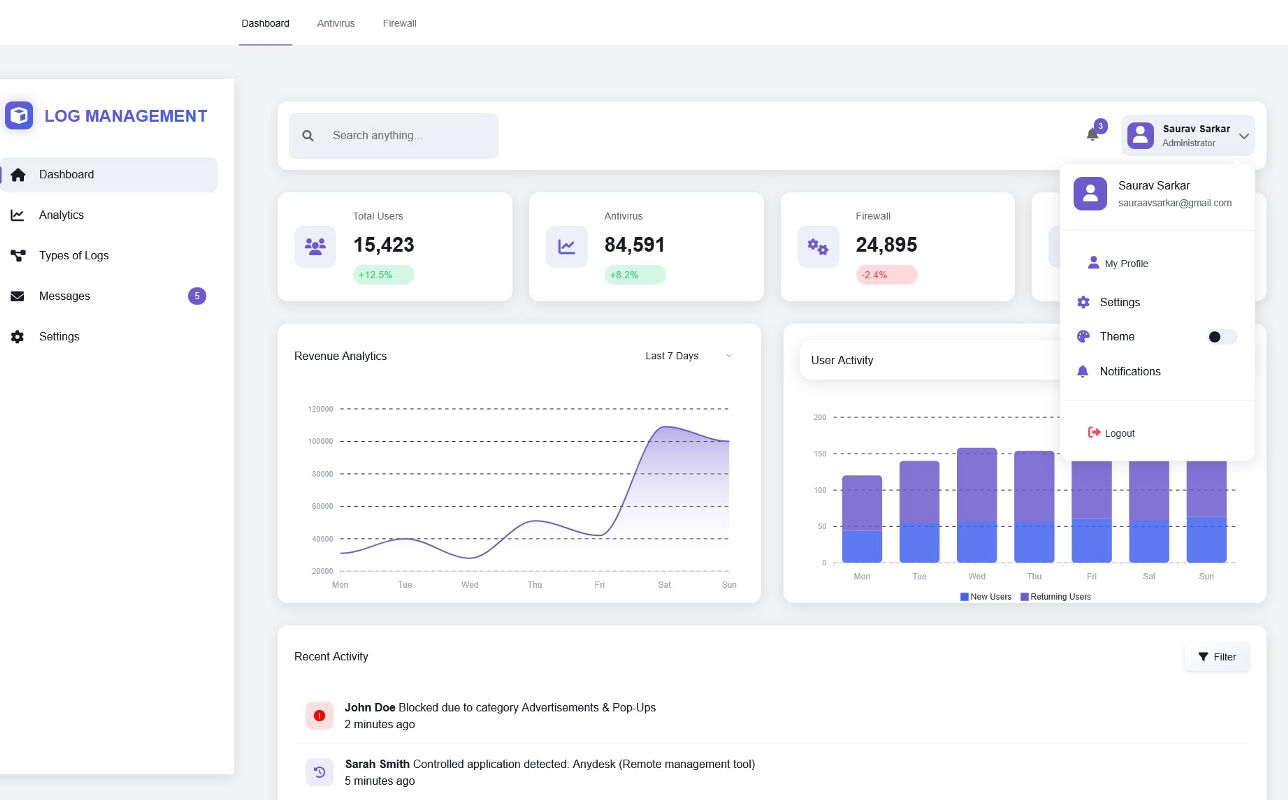
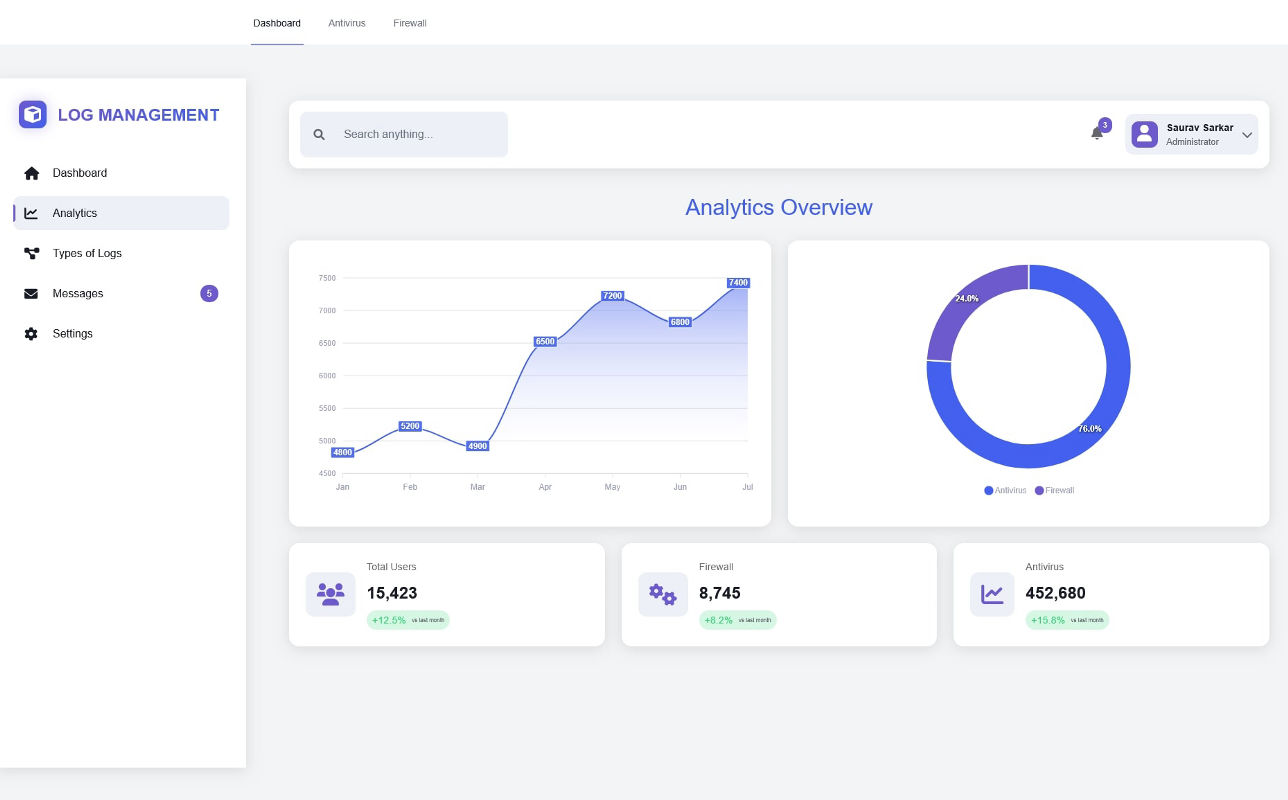
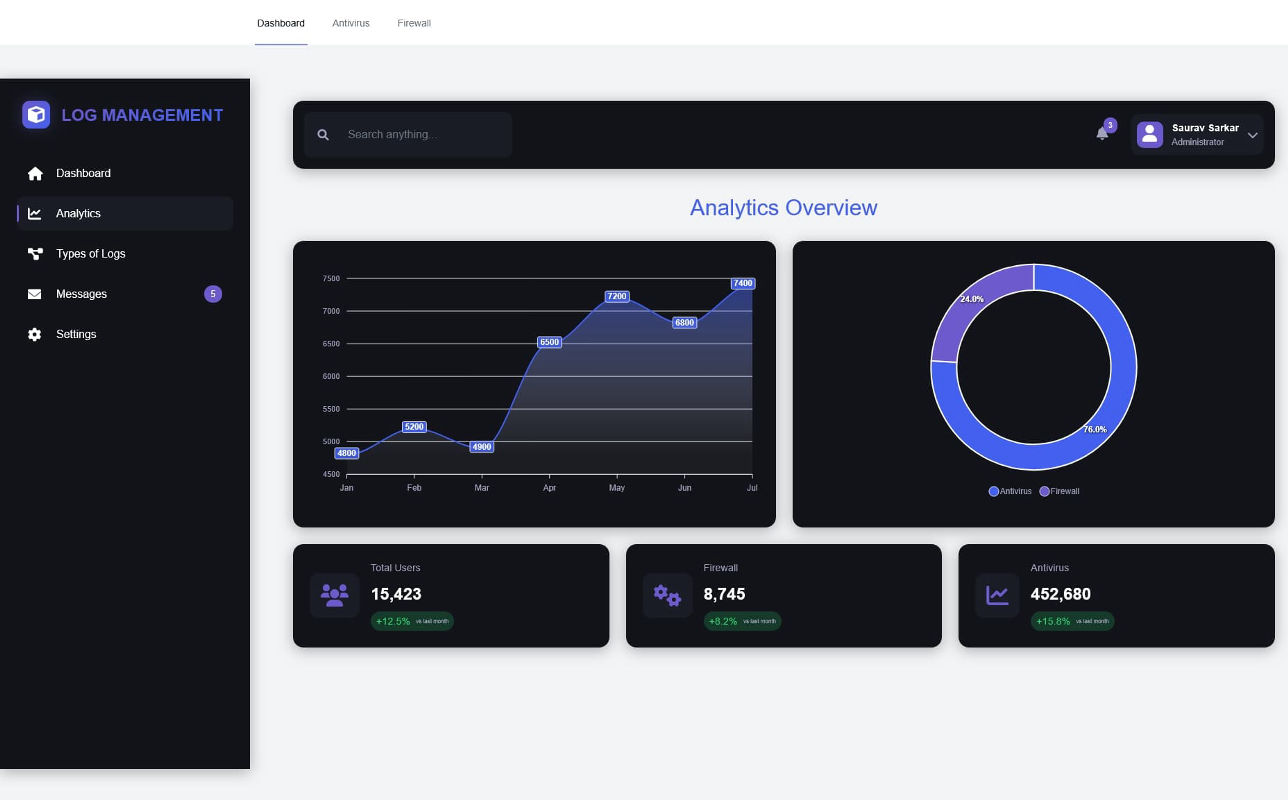
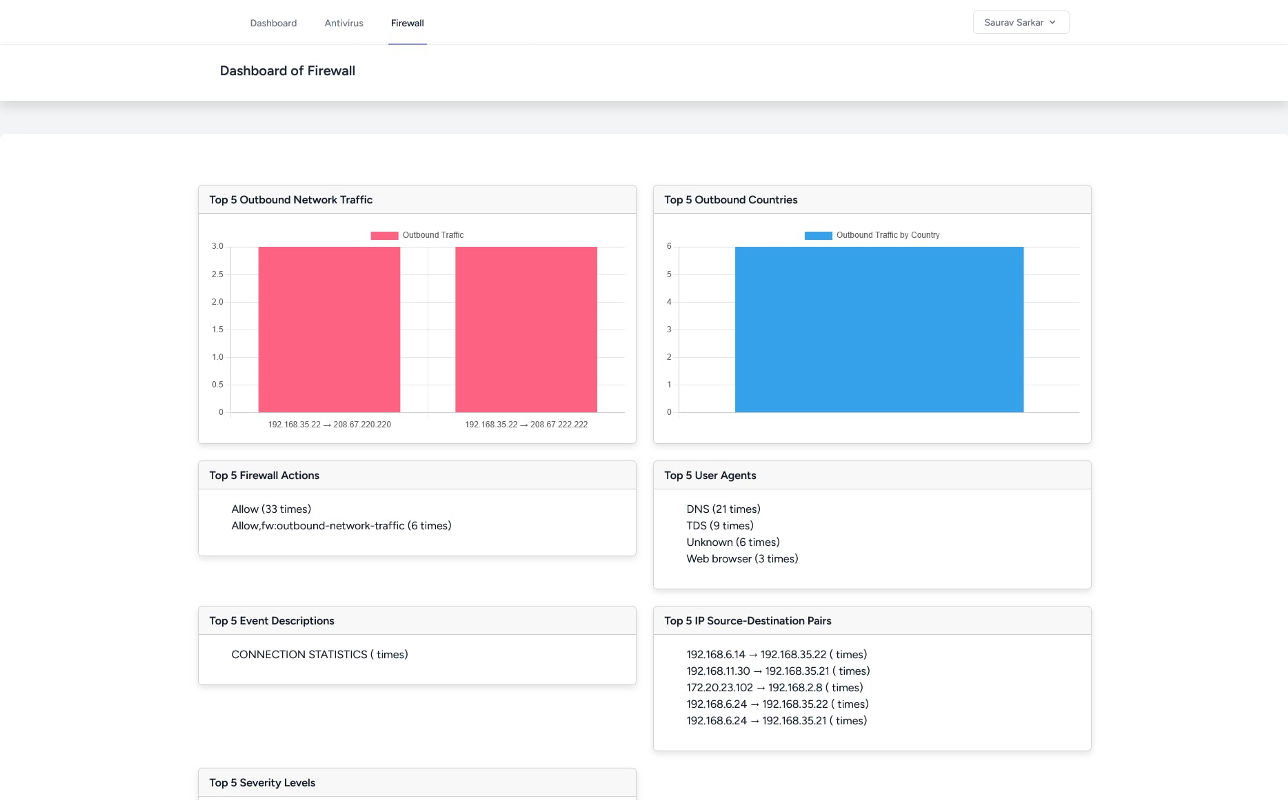
Interactive Dashboard (Chart.js)
Real-time visualizations built with Chart.js including: top failed logins, out-of-hours activity,
antivirus
alerts, high-traffic IPs, and time-based trends. Supports drill-down, exporting, date filters, and
auto-refresh.
-
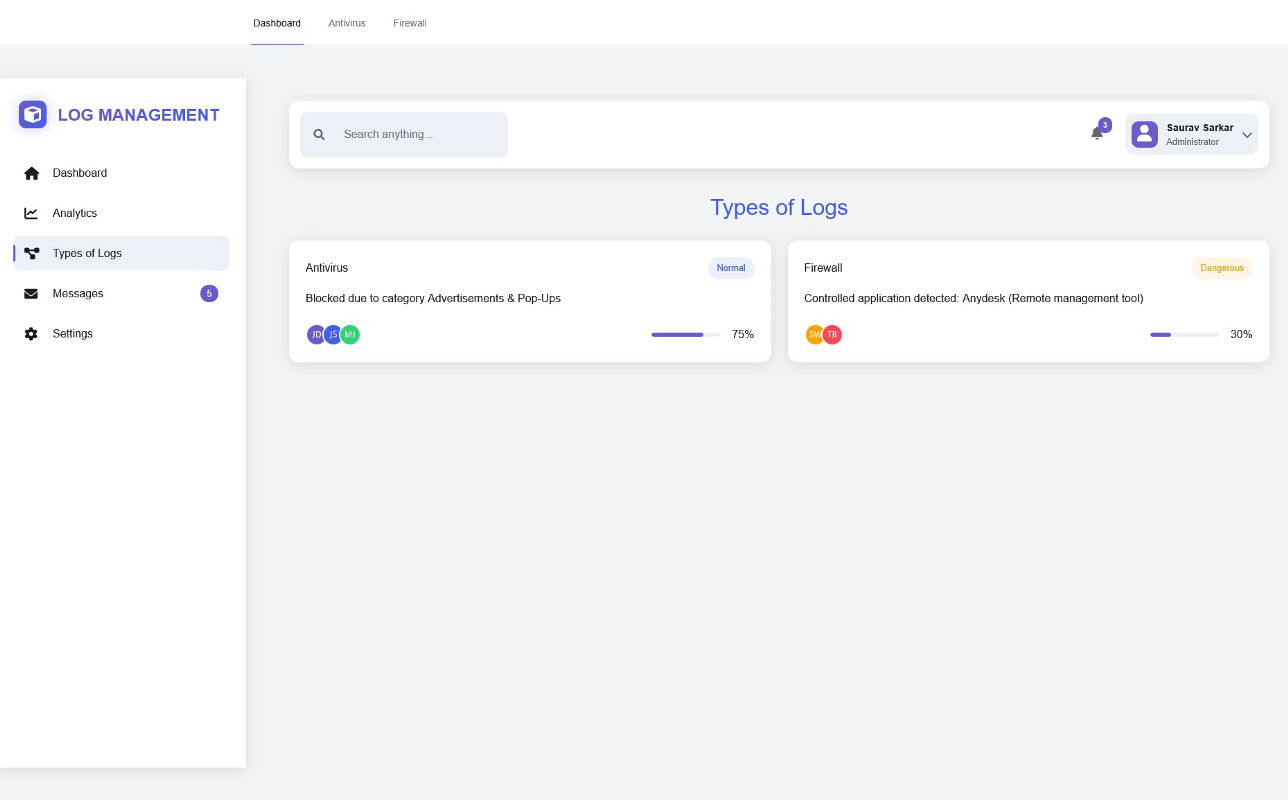
Threat Detection & Email Alerts
Rule-based detection for suspicious events, repeated login failures, malware alerts, and more.
Configurable thresholds, real-time notifications, and external threat intelligence integration.
-
Scalability & Flexibility
Dynamic table creation, flexible vendor support, SIEM integration, S3-compatible storage support,
and expandable architecture for new log sources like proxy, VPN, or DB logs.